Concepts
A set of runtime primitives for identity-governed autonomy and boundary enforceability
Placement at a glance
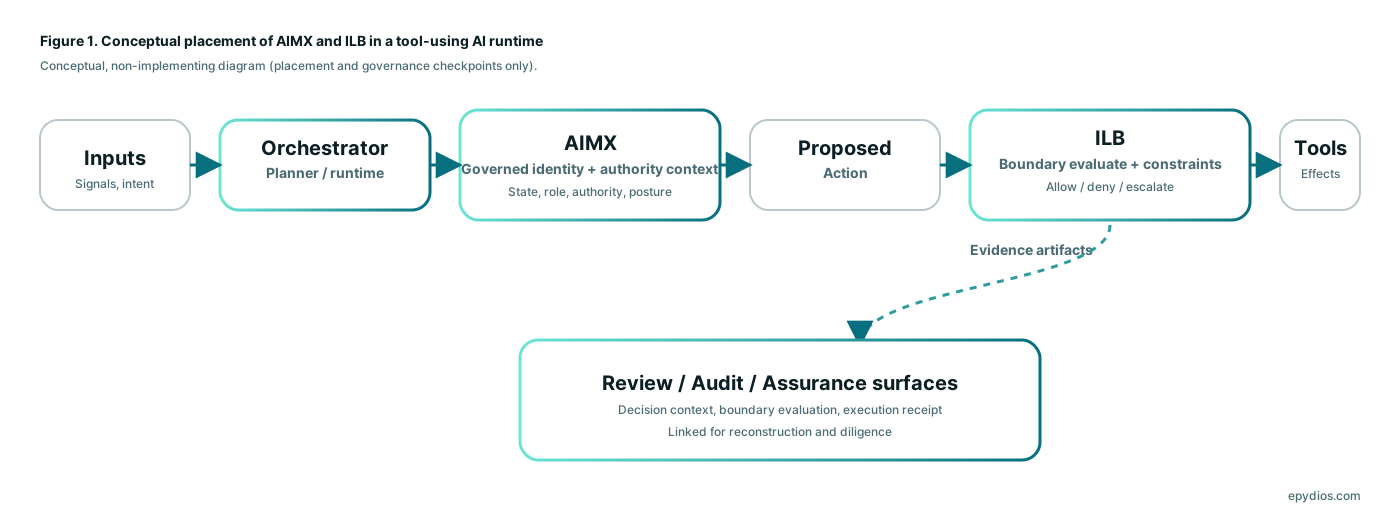
- AIMX provides governed identity state and authority context inside the runtime loop
- ILB interposes at execution interfaces and evaluates proposed actions at the moment they would take effect
APIs, schemas, message formats, integration contracts, etc. are intentionally not enumerated here.
Important Components
Identity
Who the acting entity is in the governance sense, capable of accountability.
Role
The governance-relevant stance under which an identity operates.
Authority
Scoped permission for specific action classes under conditions. Authority is contextual and separable from identity.
Posture
A governed constraint profile and escalation expectation that supports controlled transitions, such as step-up, tightening and revocation.
Action boundary
The point where a proposed action becomes an external effect. Examples include tool calls, commits, transfers, writes, control signals and other boundary-crossing operations.
Evidence artifacts
Evidence artifacts are records designed to bind decisions to outcomes. They are conceptually distinct from raw logs. The purpose is reviewability and auditability: reconstruct who acted, what was proposed, what was allowed or constrained, what executed and why.
Evidence artifacts support diligence, review, audit and incident response when deployed with clear and defined scope.
Adaptive Identity Matrix Engine (AIMX)
AIMX treats governed identity and authority as first-class runtime state.
Conceptual functions include:
- Identity representation and controlled updates
- Authority context derived from identity state and policy inputs
- Controlled transitions for escalation, tightening and revocation
- Accountability coupling through artifact categories that support review
Non-goals include replacing identity providers, acting as “just authentication” or being tied to a specific model family.
Independent Layer Boundary - Behavioral Autonomy Constraint Kernel (ILB; ILB-BACK)
ILB interposes at execution interfaces where actions become effects.
Conceptual functions include:
- Boundary evaluation at decision time
- Constraint attachment and escalation requirements
- Allow, deny or escalate outcomes grounded in identity and authority context
- Evidence artifact production linking evaluation and outcome
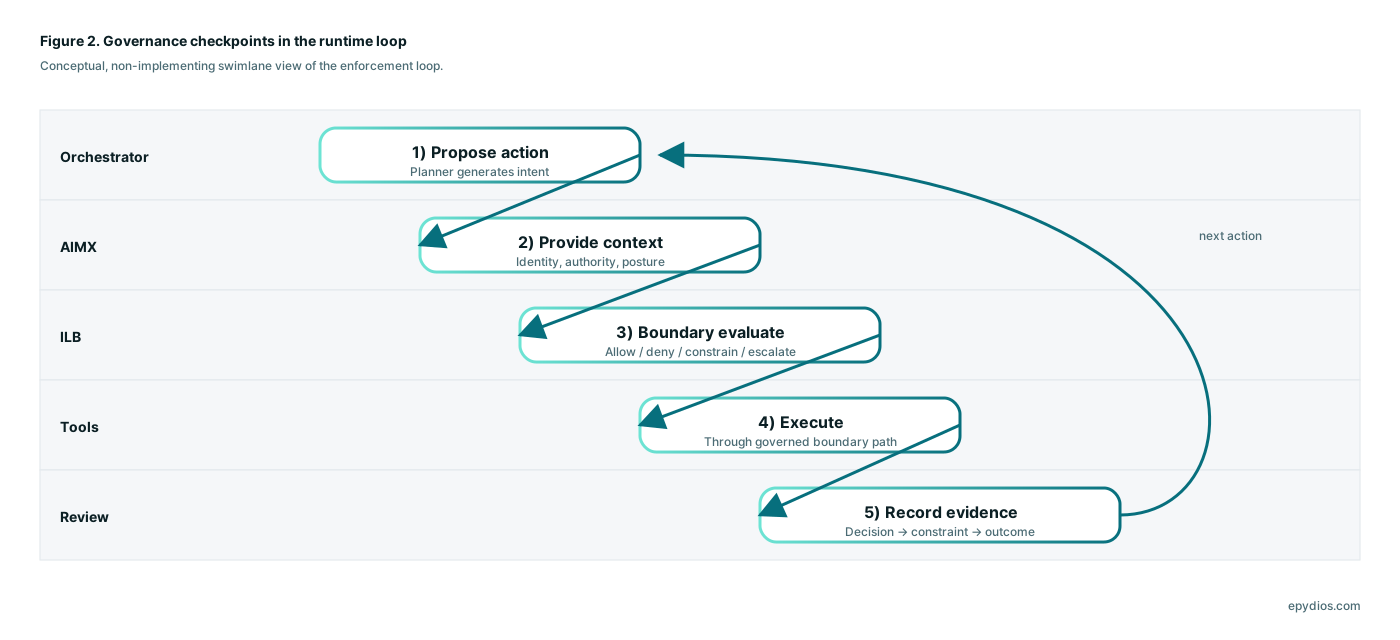
AIMX → ILB handshake
- The orchestrator proposes an action
- AIMX supplies governed identity state and authority context
- ILB evaluates at the execution boundary using context and posture
- ILB allows with constraints, denies or escalates through controlled transitions
- Execution proceeds through the governed boundary path producing evidence artifacts that bind decision to outcome
Fit with existing stacks
The architecture is designed to layer onto existing IAM, policy sources, orchestration and observability. Specific integrations are environment-dependent and out of scope here.
Limitations and non-goals
- Enforceability depends on attachment to the real execution boundary. If execution bypasses the boundary, governance is incomplete.
- This does not claim to “make the model safe.” It anchors governance where actions become effects and improves legibility and evidence quality.
